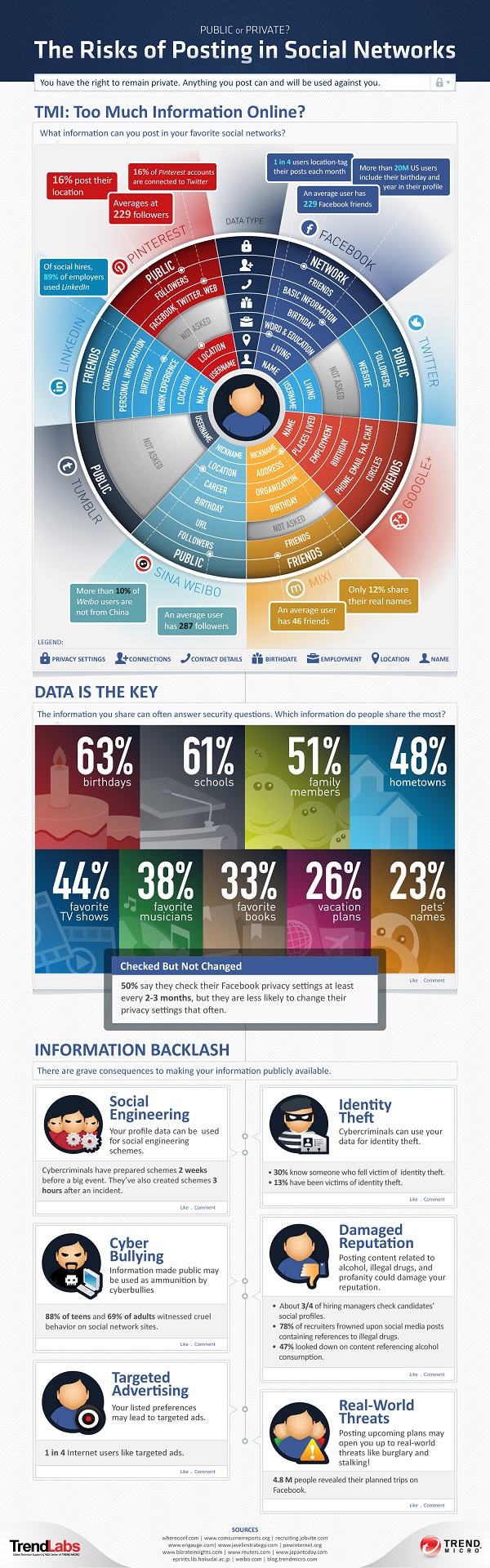
Social Media Security Fundamentals
▼LinkedIn Security + 3 Things Social Media Experts Never Tell You▼
Social Media is a Universe. Not a Site. Learn How To Win ⬆ Images Hyperlinked
Months ago, I observed a frustrated entrepreneur with a large follower base who normally gets many likes and retweets soliciting suggestions in vain. Everybody seemed silent. The issue?
Someone was repeatedly faking unfavorable reviews of her business on Yelp, and she was distraught.
As I looked closer, I realized she didn't just have a Reputation Management problem. Rules aside, she had major Cyber Risk Management issues. Unaware there's more to Social Media than networking, prospecting, customers, lead generation or profit margins?
Social Media can ruin your business if your risk intelligence as an entrepreneur is low; if, you're on LinkedIn, yet know nothing about LinkedIn Security, spotting and protecting yourself against Linked scams; outfoxing scammers of all stripes, or avoid being recruited as a spy by shady, hostile actors.
In China's case for example, even if you're not being subjected to censorship or surveillance, you may be a spy recruitment target unawares. If not being 'jobfished' — a lesson I learned in China the hard way on more than one occasion, as I gained knowledge about LinkedIn's complicity as a platform.
And it's not just academics. Which is why #iTHiNKLabs recently warned about ExecThread.com
There are malicious lurkers, stalkers, swindlers, fake or disingenuous so-called influencers, gaming social media platforms, and identity thieves (images hyperlinked, mind you). As well as cyber criminals like the Yelp imposter above. And just as the victim likely couldn't tell you what a spambot is, the average recruiter/talent acquisition manager, often a fan of LinkedIn can't wrap their heads around the technical, security and strategic implications of 711 million stolen records. Nor they often know what kind of Phishing emails targeting LinkedIn accounts are on the rise, and the advanced solutions and mitigations required.
Bottom line: You Don’t Need To Be On LinkedIn.
Regardless what creepy job ads or daft 'LinkedIn mandatory' job ads say.
Revenue streams?
Sure. But security matters too. That's why I wrote Hiring Mistakes in the Age of Big Data. And relevantly, how to deal with impersonation attacks like the above? Click or tap below or contact me.
There's a reason neither Denise Wakeman (in Part 1) nor Melinda Emerson (above) address Social Media Security. And that's because one has to understand something, and relevantly, its risk implications and associations to deem it worthy of serious consideration when advising people.
So although Melinda Emerson is on point here, I'll add actionable perspective as I expatiate on three things Social Media experts never tell you, —because in most cases, they don't know:
Social Media Security matters! And if you want to get it right, don't ask marketers.
Why? Because Cyber Security 101 (images hyperlinked), which one needs to master before even touching Enterprise Social Media Security, is hard enough for many IT folks, Security pros and professional hackers to (consistently) pass, given the countless variables at play.
Hence, the high profile and embarrassing data breach and hacking stories you often hear about. So what is Social Media Security exactly?
I define Social Media Security as the dynamic and expert art of monitoring one's critical Data Assets and Social Assets through proactive elimination or mitigation of Social Media, Social Networking, Social Engineering and associated Reputational Risks and Cyber Security threats.
Social Media Security is not achieved through verbal assurances (e.g., “we take security seriously”) or assumptions.
Your strong opinion and confidence about how 'safe' your computers systems or devices are, or how smart your IT personnel is, should be tampered by the simple fact that even FBI, CIA and NSA chiefs and intelligence agencies and officials regularly being compromised, doxed and embarrassed using Social Media.
This is why it pays to hire people with a good nose for Security. Because when we say Social Media Security, what we're really saying is: Your employees and top executives are in the frontlines.
Speaking of which, recruiting firms, who like marketers, advertisers and Social Media experts are yet to get the memo that LinkedIn, Facebook and Twitter are in fact dangerous neighborhoods where hackers and malicious actors lie in wait, are among the worst offenders.
The executives running the show in these shops are in most cases mere end users (even if considered Social Media savvy) who don't understand that knowing how to avoid unwanted Social Media attention is good Social Media Security strategy. One that warrants frequent training.
If you understand that you can't possibly prove where your data is, let alone articulate The Anatomy of a Social Media Attack, the next logical step apart from learning Social Media Security and hiring who understand the threatscape and how to properly defend yourself, is to bake the foregoing into your Social Media Strategy.
I was shocked to find most 'Social Media Trends You Need to Add to Your 2017 Strategy' publications like this one do not have a single thing to say about Social Media Security Risks.
Indeed good Social Media expert advice or consultation not only addresses WHY the foregoing matters but also warns you, with proof, that companies lose market value in millions of dollars post-breach.
Strategic Social Networking byproducts aren't always in the public domain. Be humble.
○ ○ ○
Years ago, I published a blog in which I adopted Mitch Joel's authentic definition of Social Media.
Sometime last year, I found myself discussing some of my successes with him over email.
From fully paid transcontinental C-Level consulting work, travels, etc. And that's when he wrote in agreement:
“My main thinking is this: my blog used to be the hub… now, it’s more like the archive...Keep the blog up to date and my content have a longer lifecycle with more distribution...Yep… I call this strategic byproducts… sometimes of much higher value than being paid by the word, post, etc… :)”
It's always the fake, insecure, or wannabe Social Media “expert” that ASSUMES there's some monolithic global definition of THE perfect Blog, Tweet or Social Media execution or presence.
People will try to impose their “text-based” view of a blog on you. Their hashtag intolerances, etc. Yet in the mind of a 57% Innovator/Builder Right Brainer per CVI (Core Values Index™), a blog's definition depends on the content creator's core strategy and variables best known to him.
Which is why Dr. Myles Munroe was on to something when he said in 10 Best Kept Secrets of Success: “The manufacturer is the only one who knows the truth about his product. Everybody else is experimenting. Everybody else is guessing. Everybody else has opinions.”
Whatever one's strategy or — with regard to Social Media Security — risk appetite, unless the manufacturer, artist or content creator truthfully shares it, all an opinionated onlooker has is opinions. Put differently, not everything is googleable.
Accurately verifying one's claims, identity, successes, etc. is best done by reaching out in good faith. Something smart Social Media experts and recruiters understand.
This is why as below (see #3), I'm not impressed by all that Social Proof, Online Visibility, Personal Branding and Engagement pressure and noise.
Your job is to tune out the noise; read widely, heed Denise Wakeman and Melinda Emerson plus the combined insights shared in this and other 'Strategic Social Networking Series' together with my Big Ideas & The Creative Process (From Art to Entrepreneurship) series. And so long as you're consistent and serve high quality content in good faith, you'll be fine.
Finally:
Social Proof, Online Visibility, Personal Branding and Engagement is overrated, easily exploited, based on dangerous assumptions, and brands and consumers are being robbed in the billions through digital advertising fraud while consumer data and IP is hijacked. Click/Tap:
If you've meticulously read the above, absorbed the argument, and importantly, possess and bring great business acumen rooted in ethics, then you probably, instinctively, understand why Social Proof, Online Visibility, Engagement and Personal Branding made the list. You see, Red Website Design — the creators of the infographic below — and I follow each other on Twitter.
I respect them. But I was ignoring the rules above long before we found each other as the point for me, at any given time, is to ethically connect with the right people.
Not allow your limited time, energy or precious resources to be drained by unproductive, toxic, irrelevant superficial concerns. Which is why those with a strong “inner scorecard” are content with only 1 or 2 solid, ethical followers. And if those two happen to be Bill Gates and Mother Teresa, great! Put differently:
Some of the loudest proponents of (the perverted version of) #3 are the most disingenuous and superficial characters you'll encounter on Social Media. The type that Follow you until you Follow them back only to surreptitiously Unfollow or Mute you while they push content your way.
In the last several years, Social Networking has become synonymous with greed, botnets and tech-aided fraud, disingenuous metrics and score keeping decried by the likes of Seth Godin. And among digital marketers in particular, the smug content with what Bob Hoffman terms The Golden Age of Bullshit (video)
Hoffman sees through the same game I see.
This is why he correctly observes: “The advertising industry has become the web’s lapdog – irresponsibly exaggerating the effectiveness of online advertising and social media, ignoring the abominable results of display advertising, glossing over the fraud and corruption, and becoming a de facto sales arm for the online ad industry.”
In many ways, Social Media “experts” are part of the problem because they add to a frightening abundance of naïveté and ignorance as they profit from silence on ethical and controversial issues.
Put differently, an uninformed Social Media expert doesn't live in a world where journalists, lawyers, and (human rights) activists or even sometimes business people engaged in sensitive work require unwanted Social Media attention. Their biases prevent them from understanding why young Rohingya lawyer Wai Wai Nu for example, has a private Twitter page.
These are the same people who exploit hashtags like #Leadership yet conveniently go M.I.A. during high profile (e.g., Donald Trump) leadership/power abuse and corruption incidents. To quote Bob Hoffman one last time: “Insufferable egotists pretending to be public servants.”
And so while YES, online “visibility gives you options” — anecdotal proof I've supplied throughout this article, and indeed embody, for those who know my work, is proof — Personal Branding, Engagement, Online Visibility and/or Social Proof on steroids is, and CAN be misleading baselines. Because, like Hoffman in Advertising, some of know things about the way the web works that you don't.
Like FBI Director James Comey who, until recently outed on Twitter, had only about 15 Followers there are CEOs and very discreet, Social Media influencers who are hugely more successful than the loud, shady digital marketers and companies buying followers while practicing dishonest SEO.
Just as the world's sane nations wonder how so many millions of Americans could elect a U.S. President not worthy of The Oval Office and White House, thousands and even millions on Social Media, whether real human beings or bots, can be wrong.
That's why you shouldn't be impressed by Social Proof. Because not everybody is marching to the same mainstream Social Media strategy tune, or can afford to have personally identifiable information about them pieced together by adversaries.
Just because everybody's doing something doesn't mean it's right or safe for you.
Finish below. Or for consultation, connect with me or follow me here.
○ ○ ○
Radical Cyber, Mobile & Social Media Security iQ ▼ Images Hyperlinked
Follow the Dove
How To Nail Social Media (Part 2) | Strategic Social Networking: iQ6
PEACE
TT



Comments
Post a Comment