How To Dodge The Ransomware Epidemic
▼Threat Smart V: Crypto Ransomware Mitigation & Remediation▼
FEATURE AUDIO (PLAYING) AT BOTTOM. IMAGES HYPERLINKED WITH SOLUTIONS..jpg)






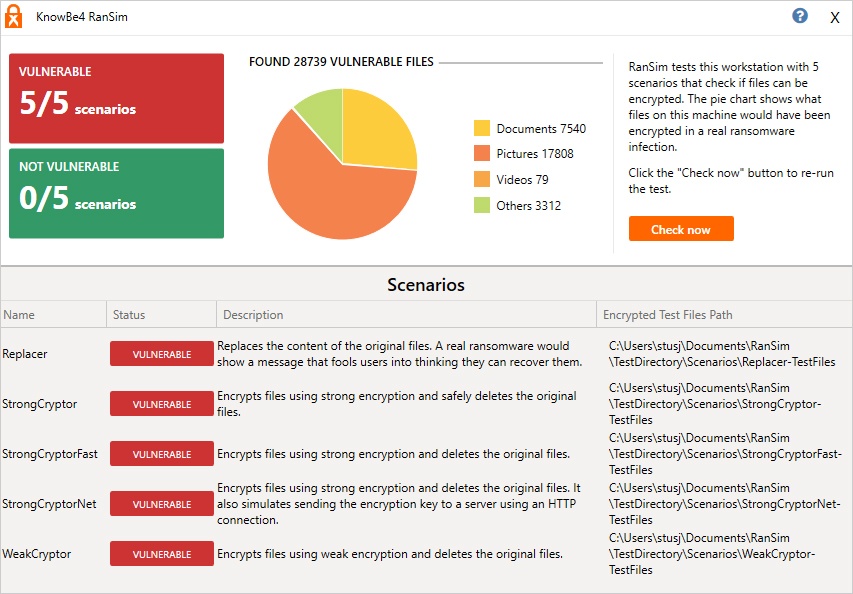


Previously published in 2016, this dynamically updated guide works best when combined with a 24/7
Cyber Security Awareness 365° posture that respects security fundamentals, —and with risk maturity
& solid attack surface & attack vectors reduction dedication, the linchpins of customer data security.
Keep unused devices disconnected. Segment networks. Shun the IoT bandwagon; Be click averse⬆
Email/web. Religiously backup data, patch, and AVOID Adobe Flash. Get Anti-Ransomware⬆ Boot
scan often. Use next-gen Cyber security/AV. And habitually encrypt, —as insurance against nasty
data leaks & dumps. Backups have their limits.⬆ Security really is very difficult & porous. Think
embedded device security. The security industry's infamous “professional” hacking group—
Hacking Team—knew security inside out, or so we thought. And yet they got pwned. PCAP
won't prevent data dumps & reputational damage! And as being off the grid isn't feasible,
you have to invest time and requisite resources in understanding, constantly reviewing,
and (re)evaluating your risk appetite. Email, as evidenced by callers' horror stories in
this blog's feature audio playing is a common attack vector. Question: How devoted
& well-trained are you and your home users/staff to maintaining a habit perpetual
suspicion online. All emails with links+attachments, be they Word docs, PDF, RTF,
Zip or image files all of which can be weaponized with malicious code, must be
be viewed with suspicion. For those in the habit of surfing banner ad-infested
shady sites for cute photos, funny cats/dogs, or dancing pig memes/videos,
porn or cracks, the party's over. You're better off investing that time read
-ing up on malvertising and installing Blur, UBlock Origin, Privacy Badger,
plus HTTPS-Everywhere, instead. Plus, enhancing your Wi-Fi Security.
Returning to Email Security, reactive, trigger-happy email habits of
the past is the easiest way to get infected. ABSOLUTELY learn to
be click averse! Best, treat Social Engineering, Spear phishing
and Phishing like a newly released, must-read, must-have or
must-see or hear trilogy, anthology, movie, video game or
TV series. And YOU—are that fanatical fan. Now go mad!
Ransomware is the proven new get-rich-quick scheme
for cybercriminals. 83% of extortion cyberattacks in
2015 came via crypto-ransomware. And 44% of UK
victims pony up. Hollywood Presbyterian Medi-
-cal Center lost 10 days of downtime as Apple
users infected were reminded a PC/device
that isn't sufficiently locked down & fully
patched with good security, including
AV/Ad-Blockers, downloading reck-
lessly from compromised sources
is 1 way to get infected. Have
a PC/device used solely for
web browsing with data
you don't mind losing
& backup twice or
weekly to other
unconnected
○ ○ ○
Don't Pay! But Know WHEN To Negotiate | High Impact Strategic Business Sense (6m)
⬆ IBM Ransomware Incident Response Guide (Above) | Images Hyperlinked
PEACE
TT
F I N I S





Comments
Post a Comment